
Enterprise Security user interface
Go to the address indicated in connection with the delivery.
Login and use of the user interface view
Specify the address in your browser. Enter the username and password provided to you. You use your SurfManager Customer username and password to log into the application.
Figure. Login.
The overview appears. From the tabs at the top of the page, you can view information on the selected firewall, such as firewall statistics, firewall rules, etc. You can find the various services in the table. You can select a service to see a more detailed overview of the service and the specifications to be made.
Figure. Overview.
Change management instructions are available here
Services
4 Antivirus protection, Advanced Threat Protection and Anti-Spyware
6.2 Antivirus and Anti-Spyware messages
6.3 Application control messages
1 Firewall rules
Firewall rules filter traffic between two data communications networks, for example the company’s LAN or subscriber line and the Internet, as specified in the firewall rules.
You can open the firewall rule base view from the Policies tab. On the left side of the page, you can select a rule base policy. A sample rule base and more detailed information on the composition of a rule are presented in the figure below.

Figure. Overview of a firewall rule base.
Rule number
Rule number is the point in the rule base where the rule is read. The firewall checks the rule base against the connection details in sequential order and stops when it finds a match.
Rule name (Name)
The name of the rule. The name will remain unchanged in the rule base.
Rule type (Type)
The rule type defines how traffic between different zones functions. The available alternatives are:
· Intrazone: traffic inside the same zone
· Interzone: traffic between defined zones
· Universal: traffic between all zones specified in the rules
Source zone (Zone)
The rule’s source zone.
Source address (Address)
Source addresses can be individual IP addresses, IP network addresses or object groups including several IP addresses, networks or groups. Geographical protection can also be specified in the Source Address field.
Source user (User)
Source users can include users, user groups, devices and device groups obtained from the user directory.
Destination zone (Zone)
The rule’s destination zone.
Destination address (Address)
Destination addresses can be individual IP addresses, IP network addresses or object groups including several IP addresses, networks or groups. Geographical protection can also be specified in the Destination Address field.
Application (Applications)
The applications permitted by the rule. A more detailed list can be found at https://applipedia.paloaltonetworks.com/ or under firewall management.
Service and URL category (Service)
The TCP/UDP port(s), service(s) and group(s) to be used are specified in the service. The web categories used for the rule are specified in the URL category. The web categories can be found at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the table found in the web content filtering instructions.
Action (Action)
The action is specified using one of the following options:
· Allow, i.e. permit the traffic.
· Deny, i.e. reject the traffic. This differs from Drop in that the firewall informs the party attempting to establish a connection about the disconnection.
· Drop, i.e. block the traffic.
Profile
Profiles can be used if traffic has been allowed in the Action field. Profiles are specified for Antivirus/Anti-Spyware, Intrusion Prevention and Web Content Filtering traffic. Each profile is specified individually. Specify the name of the used profile in the policy. The functionalities related to profiles are described in more detail in their own sections.
Rule tracking (Options)
Specify whether or not a log will be kept of connections that activate the rule.
Return to the service selection table
2 Network address translation
NAT (network address translation) rules specify which addresses or services are to be translated into which addresses or services. The rules are similar to those used in a standard rule base to specify the traffic to be allowed or blocked.
You can access the NAT rule view by selecting NAT on the Policies tab.
A NAT rule and more detailed information on the composition of a rule are presented in the figure below.
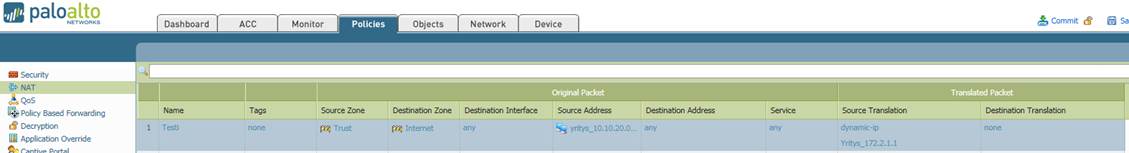
Figure. NAT rule.
Rule number (No)
Rule number is the point in the rule base where the rule is read. The firewall checks the rule base against the connection details in sequential order and stops when it finds a match.
Rule name (Name)
The name of the rule. The name will remain unchanged in the rule base.
Original source zone (Source Zone)
The original source zone used.
Original destination zone (Destination Zone)
The original destination zone used.
Original interface (Destination Interface)
The original interface used.
Original source address (Source Address)
The original source address used. It can be an individual IP address or IP network, or an object group including several IP addresses, IP networks or groups.
Original destination address (Destination Address)
The original destination address used. It can be an individual IP address or IP network, or an object group including several IP addresses, networks or groups.
Original service (Service)
The TCP/UDP port, service or group to be used are specified in the service.
Translated source address (Source Translation)
The translated source address. It can be an individual IP address or IP network, or an object group including several IP addresses, IP networks or groups.
Translated destination address (Destination Translation)
The translated destination address. It can be an individual IP address or IP network, or an object group including several IP addresses, networks or groups.
Return to the service selection table
3 Web content filtering
Web content filtering compares the URL (Uniform Resource Locator) of a downloaded Internet page with a database where web pages are pre-categorised into certain page categories. This functionality allows users to be informed in real time of web traffic restrictions, the risks of the Internet, and the security policy of the organisation.
You can access the web content filtering rule base view by selecting URL Filtering on the Objects tab. In addition, the functioning of web content filtering requires that the profile being used has been specified in the Profile option of the rule base policy.
A web content filtering rule and more detailed information on the composition of a rule are presented in the figure below.
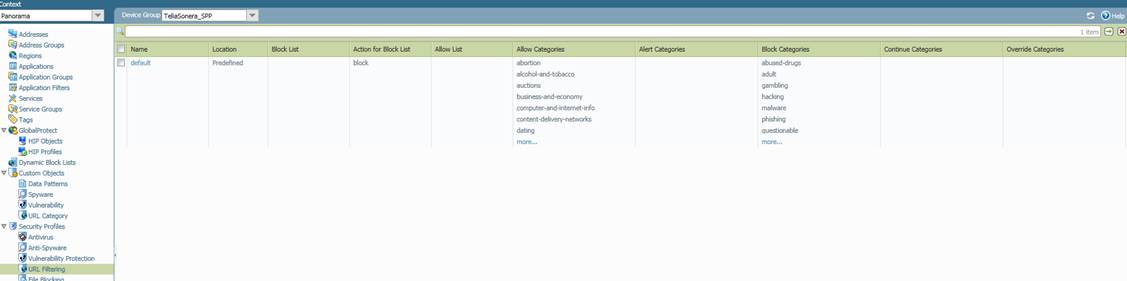
Figure. Web content filtering rule.
Profile name (Name)
The name of the profile. The profile name will be used in the policy’s profile definition.
Blocked addresses (Block List)
This setting specifies which addresses will be blocked.
Action towards blocked addresses (Action for Block List)
Action taken for traffic from blocked addresses. The available alternatives are:
· Allow, permit the traffic
· Block, prevent the traffic and notify the user
· Alert, permit the traffic but record an alert in the web content filtering log
· Continue, request confirmation from the user before opening the website
· Override, permit the traffic if the user enters a password
Allowed addresses (Allow List)
This setting specifies which addresses will be allowed.
Allowed categories (Allow Categories)
This setting specifies which categories will be allowed. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Categories that will cause an alert to be logged (Alert Categories)
This setting specifies which categories will cause an alert to be recorded in the log. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Blocked categories (Block Categories)
This setting specifies which categories will be blocked. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Categories requiring confirmation from the user (Continue Categories)
This setting specifies the categories whose traffic requires the user’s approval in the rules (Response Page). All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
Categories requiring the user to enter a password (Override Categories)
This setting specifies the categories whose traffic requires the user to enter a password. All users share the same password. All categories can be viewed at http://www.brightcloud.com/tools/change-request-url-categorization.php and in the Listing table below.
The web content filtering categories are listed in the table below.
|
BrightCloud categories |
|||
|
Abortion |
Government |
Motor Vehicles |
Search Engines |
|
Abused Drugs |
Gross |
Music |
Sex Education |
|
Adult and Pornography |
Hacking |
News and Media |
Shareware and Freeware |
|
Alcohol and Tobacco |
Hate and Racism |
Nudity |
Shopping |
|
Auctions |
Health and Medicine |
Online Greeting cards |
Social Network |
|
Bot Nets |
Home and Garden |
Parked Domains |
Society |
|
Business and Economy |
Hunting and Fishing |
Pay to Surf |
Sports |
|
CDNs |
Illegal |
Peer to Peer |
Spyware and Adware |
|
Cheating |
Image and Video Search |
Personal Storage |
Stock Advice and Tools |
|
Computer and Internet Info |
Internet Communications |
Personal sites and Blogs |
Streaming Media |
|
Computer and Internet Security |
Internet Portals |
Philosophy and Political Advocacy |
Swimsuits and Intimate Apparel |
|
Cult and Occult |
Job Search |
Phishing and Other Frauds |
Training and Tools |
|
Dating |
Keyloggers and Monitoring |
Proxy Avoid and Anonymizers |
Translation |
|
Educational Institutions |
Kids |
Questionable |
Travel |
|
Entertainment and Arts |
Legal |
Real Estate |
Violence |
|
Fashion and Beauty |
Local Information |
Recreation and Hobbies |
Weapons |
|
Financial Services |
Malware Sites |
Reference and Research |
Web Advertisements |
|
Gambling |
Marijuana |
Religion |
Web Hosting Sites |
|
Games |
Military |
SPAM URLs |
Web based email |
Figure. Web content filtering categories.
Return to the service selection table
4 Antivirus protection, Advanced Threat Protection and Anti-Spyware
The antivirus service scans the files downloaded through the firewall and prevents any malware from entering the customer network according to the company’s scanning policy. The antivirus service supports the most common web browsing, data transmission and email protocols. The user receives a user message if any viruses detected. The firewall updates the virus database automatically from the manufacturer’s update servers.
The Advanced Threat Protection service monitors how a file behaves in a workstation environment and attempts to prevent unknown malware from entering the customer network. Specify in the antivirus settings whether unknown files will be scanned or not.
The Anti-Spyware function must also be specified in the antivirus settings. Anti-Spyware detects the downloading of unauthorised programs that send user information and traffic from spyware programs already installed on the computer. Anti-Spyware also identifies known malware domains, blocking Botnet traffic.
The Antivirus and Anti-Spyware view can be accessed by selecting Antivirus or Anti-Spyware on the Objects tab.
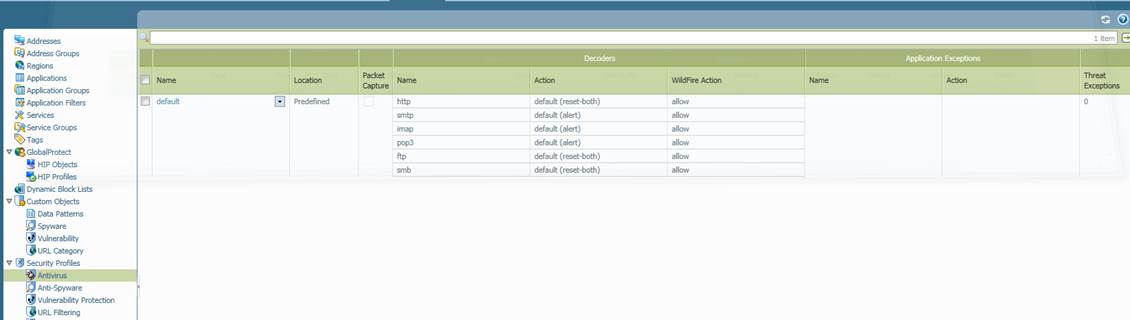
Figure. Antivirus service
4.1 Antivirus profile
The antivirus profile located on the Objects tab under the Antivirus option and descriptions of the settings specified in the profile are presented in the figure below.

Figure. Antivirus profile.
Profile name (Name)
The name of the profile. The profile name will be used in the policy’s profile definition.
Packet scanning (Packet Capture)
This setting specifies whether packets matching the profile will be scanned or not. The available alternatives are:
Yes or No (default).
Scanned protocols (Name)
Specify the protocols to be scanned. The available alternatives are:
http, smtp, imap, pop3, ftp, smb or all protocols (any)
Action for scanned protocols (Action)
This setting specifies what action will be taken if a virus is detected in a protocol being scanned. The available alternatives are: Alert, Block (default) and Allow. Actions can be individually specified for each protocol.
Definition of Advanced Threats (WildFire Action)
This setting specifies whether or not files will be sent for scanning if their function is not known. The available alternatives are: Yes (default if the service is enabled) or No. Actions can be individually specified for each protocol.
Definition of application exceptions (Name)
Specify any applications for which you would like to make exceptional specifications. The exception will apply to the entire profile. A list of applications is available at https://applipedia.paloaltonetworks.com/
Action for application exceptions (Action)
This setting specifies the action that will be taken if an application exception is detected. The available alternatives are: Alert, Block and Allow.
Definition of file exceptions (Threat exceptions)
This setting specifies files that will not be scanned.
Return to the service selection table
4.2 Anti-Spyware profile
The Anti-Spyware profile located on the Objects tab under the Anti-Spyware option and descriptions of the settings specified in the profile are presented in the figure below.
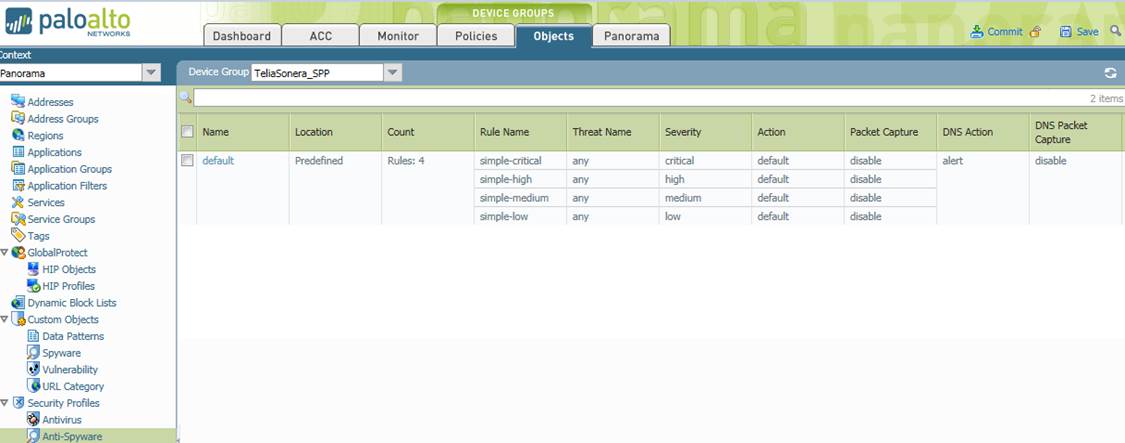
Figure. Anti-Spyware profile.
Profile name (Name)
The name of the profile. The profile name will be used in the policy’s profile definition. Several rules can be defined for each profile.
Rule counter (Count)
Indicates the number of rules in the profile.
Rule name (Rule Name)
Specify a name for the rule. The rule must specify the Threat Name (default any), level of severity, action, packet scanning, blocking of DNS queries to known malware domains and DNS packet scanning.
Threat name (Threat Name)
Specify the name of the threat being scanned for. The default setting is all threats (any). A list of threats is available at https://threatvault.paloaltonetworks.com/. Please note: this is a rule-name-specific specification.
Category (not displayed in the rule above)
Specify the categories of traffic that will be scanned. The options are: Any (all, default setting), Adware, Backdoor, Botnet, Browser-hijack, Data-theft, Keylogger, Net-worm
p2p-communication and Spyware. Please note: this is a rule-name-specific specification.
Level of severity (Severity)
Specify the severity of traffic that will be scanned. The options are: Any, Critical, High, Medium, Low and Informational. Please note: this is a rule-name-specific specification.
Action for scanned level of severity (Action)
Specify what action will be taken for traffic of a level of severity that initiates scanning. The options are: Alert, Block (default) and Allow. Please note: this is a rule-name-specific specification.
Packet scanning (Packet Capture)
Specify whether packets triggering a rule will be scanned or not. The available alternatives are: Yes or No. Please note: this is a rule-name-specific specification.
DNS query blocking (DNS Action)
Specify whether DNS queries to known malware domains will be blocked or not. The available alternatives are: Yes (default) or No. This is a profile-specific specification.
DNS packet scanning (DNS Packet Capture)
Specify whether or not a blocked packet will be scanned. The available alternatives are: Yes (default) or No. This is a profile-specific specification.
Anti-Spyware exceptions (not displayed in the sample rule above)
This setting specifies exceptional actions taken for certain threats. This is a profile-specific specification. A list of threats is available at https://threatvault.paloaltonetworks.com/.
Action for exceptional specification (Action)
This setting specifies the action taken for threats for which an exception has been set in the rules. The available alternatives are: Alert, Block (default) and Allow.
Return to the service selection table
5 Intrusion prevention
The Intrusion Prevention (IPS) functionality allows the firewall to detect any intrusion and attack attempts in the connections passing through it.
The IPS functionality detects, for example, network worms, Trojans and targeted attacks towards vulnerable applications.
You can access the intrusion prevention view by selecting Vulnerability Protection on the Objects tab. The figure below presents a profile scan and descriptions of the settings that can be made in the fields.
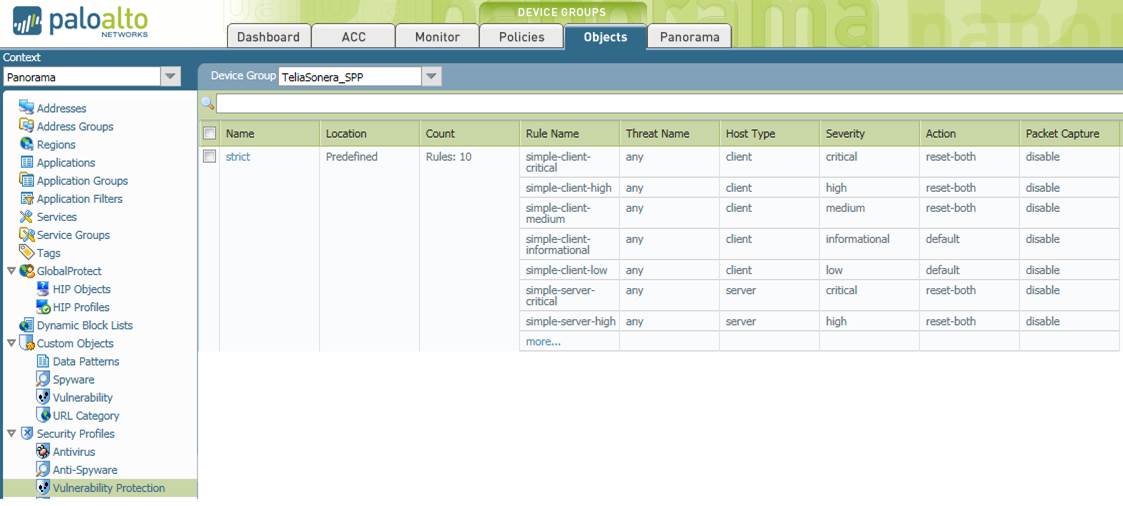
Figure. Intrusion Prevention profile.
Profile name (Name)
The name of the profile. The profile name will be used in the policy’s profile definition. Several rules can be defined for each profile.
Rule counter (Count)
Indicates the number of rules in the profile.
Rule name (Rule Name)
Specify a name for the rule. The rule must specify the Threat Name (default any), Client or Server scan, level of severity, action and packet scanning.
Threat name (Threat Name)
Specify the name of the threat being scanned for. The default setting is all threats (any). A list of threats is available at https://threatvault.paloaltonetworks.com/. Please note: this is a rule-name-specific specification.
Scanned device type (Host Type)
Specify whether traffic to clients, servers or both will be scanned. Please note: this is a rule-name-specific specification.
Level of severity (Severity)
Specify the severity of traffic that will be scanned. The options are: Any, Critical, High, Medium, Low and Informational. Please note: this is a rule-name-specific specification.
Action for scanned level of severity (Action)
Specify what action will be taken for traffic of a level of severity that initiates scanning. The options are: Alert, Block (default) and Allow. Please note: this is a rule-name-specific specification.
Packet scanning (Packet Capture)
Specify whether packets triggering a rule will be scanned or not. The available alternatives are: Yes or No. Please note: this is a rule-name-specific specification.
Return to the service selection table
6 User messages
User messages can be used to notify users of detected viruses, blocked applications and forbidden or restricted web traffic.
6.1 Web filtering messages
Web filtering messages can be used to notify users of forbidden web traffic or request confirmation or passwords from users for traffic involving websites in a certain category. The block and user confirmation views are presented in the figures below.
Figure. Block page
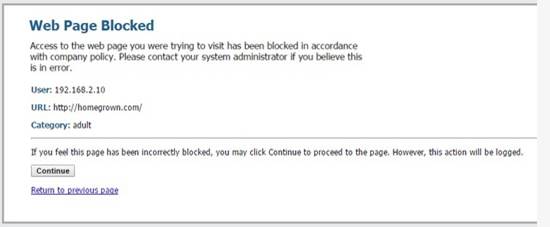
Figure. Continue page
The message contents of the above messages and the password request message can be freely defined.
Return to the service selection table
6.2 Antivirus and Anti-Spyware messages
Antivirus and Anti-Spyware messages are used to notify users of potential viruses. The user message is presented in the figure below.
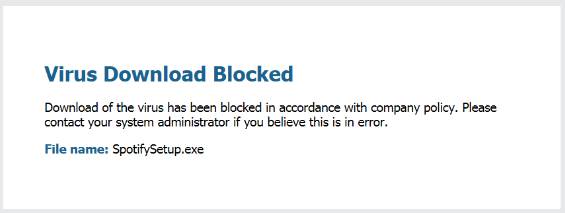
Figure. Antivirus observation message
The message contents of the above message can be freely defined.
Return to the service selection table
6.3 Application control messages
Application control messages are used to notify users of forbidden applications specified by the organisation. The user message is presented in the figure below.
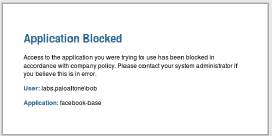
Figure. Application control user message for forbidden sites
The message contents of the above message can be freely defined.
Return to the service selection table